Army forces create and exploit informational power similarly to the joint force through five information activities (enable, protect, inform, influence, and attack). Army forces also consider information as a dynamic of combat power employed with mobility, firepower, survivability, and leadership to achieve objectives during armed conflict. Combat power is the total means of destructive and disruptive force that a military unit/formation can apply against an enemy at a given time (JP 3-0). As a dynamic of combat power, Army forces fight for, defend, and fight with information.
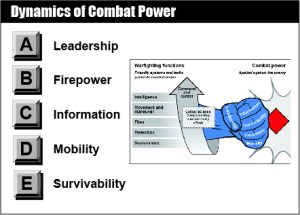
Army leaders at every level require and use information to seize, retain, and exploit the initiative and achieve decisive results. Army forces collect, process, and analyze data and information from all domains to develop understanding, make decisions, and apply combat power against enemy forces. Army forces fight for information about the enemy and terrain through reconnaissance and surveillance, and through offensive operations such as movement to contact or reconnaissance in force. Intelligence and cyberspace operations penetrate enemy networks and observe activities to gain and exploit information on the threat. Simultaneously, Army forces defend their own networks to secure friendly data and ensure secure communications. Friendly security operations, operations security, counterintelligence, and defensive cyberspace operations deny enemy access to friendly information and intentions.
Army forces fight with information to influence threat behavior. Creatively employing and concealing information can enable Army forces to achieve surprise, cause enemy forces to misallocate or expend combat power, or mislead enemy forces as to the strength, readiness, locations, and intended missions of friendly forces. Army forces also employ information as a means of amplifying the psychological effects of disruptive and destructive physical force to erode morale, impede decision making, and increase uncertainty among enemy forces. Army forces employ all relevant capabilities to attack threat data, information, and networks to hinder the threat’s ability to exercise C2.
 This article is an extract from "INFO2 SMARTbook: Information Advantage (Activities, Tasks & Capabilities)" by The Lightning Press. Download a free PDF sample and learn more at: INFO2 SMARTbook: Information Advantage (Activities, Tasks & Capabilities).
This article is an extract from "INFO2 SMARTbook: Information Advantage (Activities, Tasks & Capabilities)" by The Lightning Press. Download a free PDF sample and learn more at: INFO2 SMARTbook: Information Advantage (Activities, Tasks & Capabilities).
Browse additional military doctrine articles in our SMARTnews Blog & Resource Center.
About The Lightning Press SMARTbooks. Recognized as a “whole of government” doctrinal reference standard by military, national security and government professionals around the world, SMARTbooks comprise a comprehensive professional library. SMARTbooks can be used as quick reference guides during operations, as study guides at education and professional development courses, and as lesson plans and checklists in support of training. Browse our collection of Military Reference SMARTbooks to learn more.