Critical infrastructure protection (CIP) is a concept that relates to the preparedness and response to serious incidents that involve the critical infrastructure of a region or nation. The American Presidential directive PDD-63 of May 1998 set up a national program of “Critical Infrastructure Protection”.
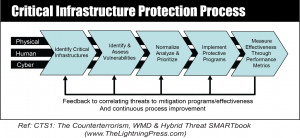
The national Critical Infrastructure Protection program is based on a risk management framework. It is continuously influenced by the ever changing threat environment, both physical and natural. The goal is to reduce the vulnerabilities to our nation’s assets from attack and natural disaster. The same methodology used at the national level can be used by garrison, installation, and command staffs as part of the ongoing process of narrowing down the list or set of assets that are critical. The five steps are explained below:
1. Identify Critical Assets
The first step will be to identify the critical assets located within your area of responsibility. The process should be an ongoing with constant review of unit missions, higher headquarters missions and requirements, as well as the overall operations within your location. The information collected should be used as the base for further discussion.
2. Identify and Assess Vulnerabilities
Vulnerability assessments should be conducted on those items identified in step 1. Potential areas of weakness need to be identified as well as protective measures that need to be undertaken to mitigate those vulnerabilities. Interdependencies within and between infrastructures need to be identified to minimize cascading effects. The vulnerability assessment needs to take into account effects which might cascade into other organizations.
3. Normalize, Analyze, and Prioritize
The staff or group accumulating the vulnerability assessments needs to normalize the information from each subordinate section or staff, and then prioritize against all of the assets the higher organization is responsible for. This step will identify which areas offer the greatest risk and the best benefit from protective measures.
4. Implement Protective Programs
The information gathered during the process will assist in developing and executing programs to protect or minimize damage to infrastructures. The staff or organization can find assistance in developing programs from their higher headquarters or through various federal agencies such as the Department of Homeland Security (DHS).
5. Measure Performance
Metrics need to be established for each protective measure to ensure they are being performed consistently, are sustainable and are effective. Continuous review of the metrics will result in improvements to the framework and the protection plan.
 This article is an extract from “CTS1: The Counterterrorism, WMD & Hybrid Threat SMARTbook (Guide to Terrorism, Hybrid & Emerging Threats)” by The Lightning Press. Download a free PDF sample and learn more at: CTS1: The Counterterrorism, WMD & Hybrid Threat SMARTbook (Guide to Terrorism, Hybrid & Emerging Threats)“
This article is an extract from “CTS1: The Counterterrorism, WMD & Hybrid Threat SMARTbook (Guide to Terrorism, Hybrid & Emerging Threats)” by The Lightning Press. Download a free PDF sample and learn more at: CTS1: The Counterterrorism, WMD & Hybrid Threat SMARTbook (Guide to Terrorism, Hybrid & Emerging Threats)“
Browse additional military doctrine articles in our SMARTnews Blog & Resource Center.
About The Lightning Press SMARTbooks. Recognized as a “whole of government” doctrinal reference standard by military, national security and government professionals around the world, SMARTbooks comprise a comprehensive professional library. SMARTbooks can be used as quick reference guides during operations, as study guides at education and professional development courses, and as lesson plans and checklists in support of training. Browse our collection of Military Reference SMARTbooks to learn more.